Revolutionizing Cybersecurity: Unveiling the Power of the P55 System for Enhanced Authentication and Security

In previous articles, we have proudly stated that the P55 system is both revolutionary and unbreakable, comparing it to its closest rival, SHA512. Let's delve into what this revolutionary system can do, particularly in the realm of authentication, and how it applies to Multi-factor Authentication (MFA).
Firstly, I realize I haven't fully explained what P55 is. So, let's address that. The P55 system comprises three components: the generator, the verifier, and the technology. A key aspect of this system is that the calculations leave no residual information needing storage. They operate autonomously and retain no data.
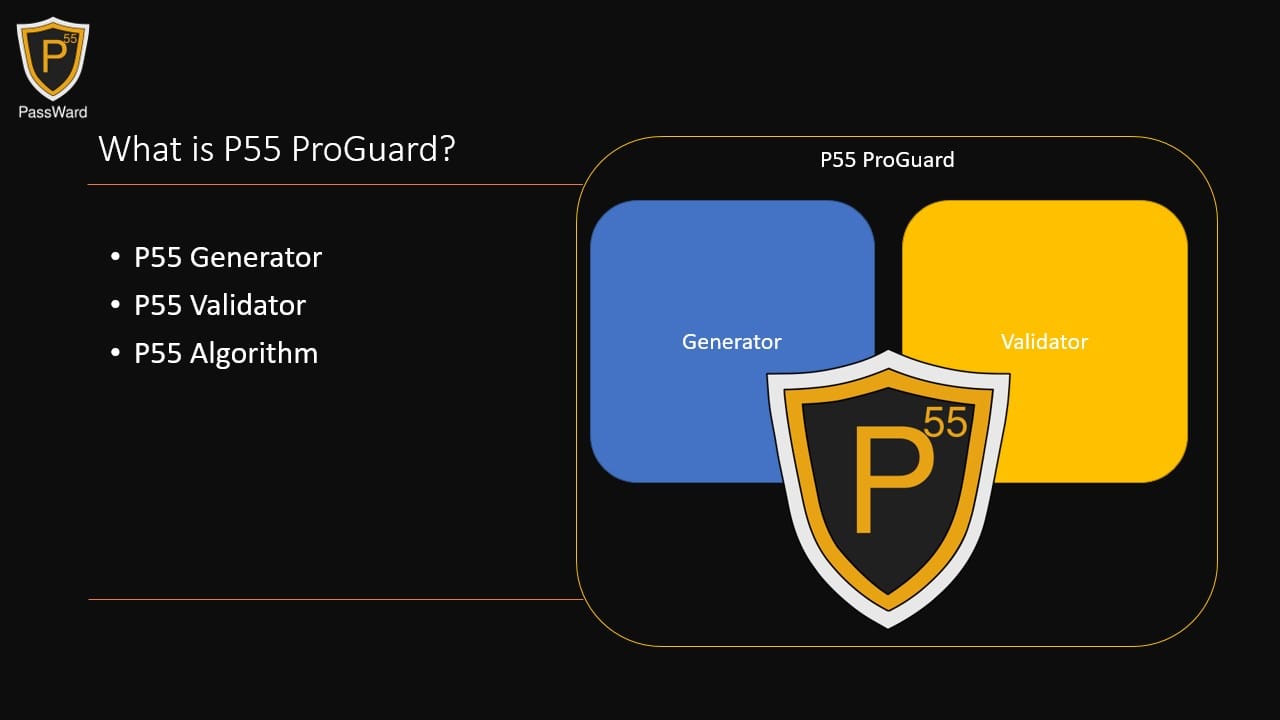
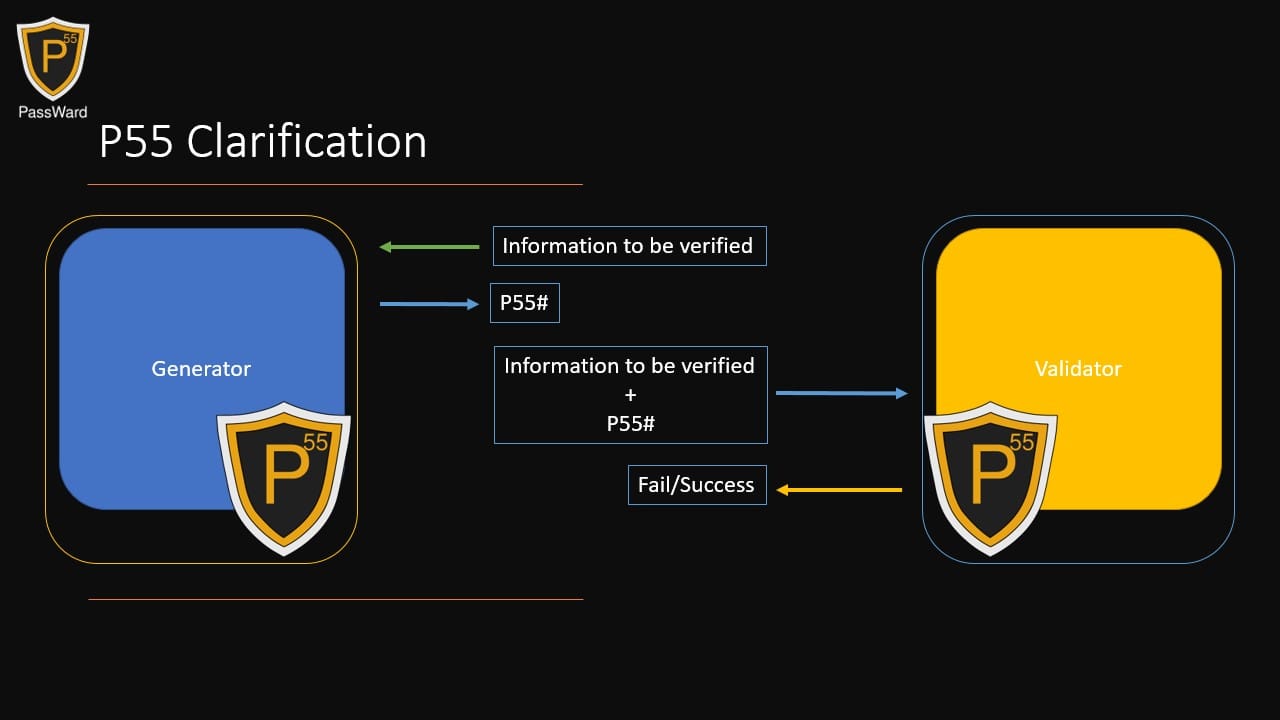
The P55 ProGuard system encompasses these three elements in a single package. However, due to the modular and dynamic nature of the technology, it's possible to separate the generator from the verifier, placing them in two distinct environments. As long as they operate on the same version of the technology, they only require the specific information to be verified and the P55 hash produced by the generator.
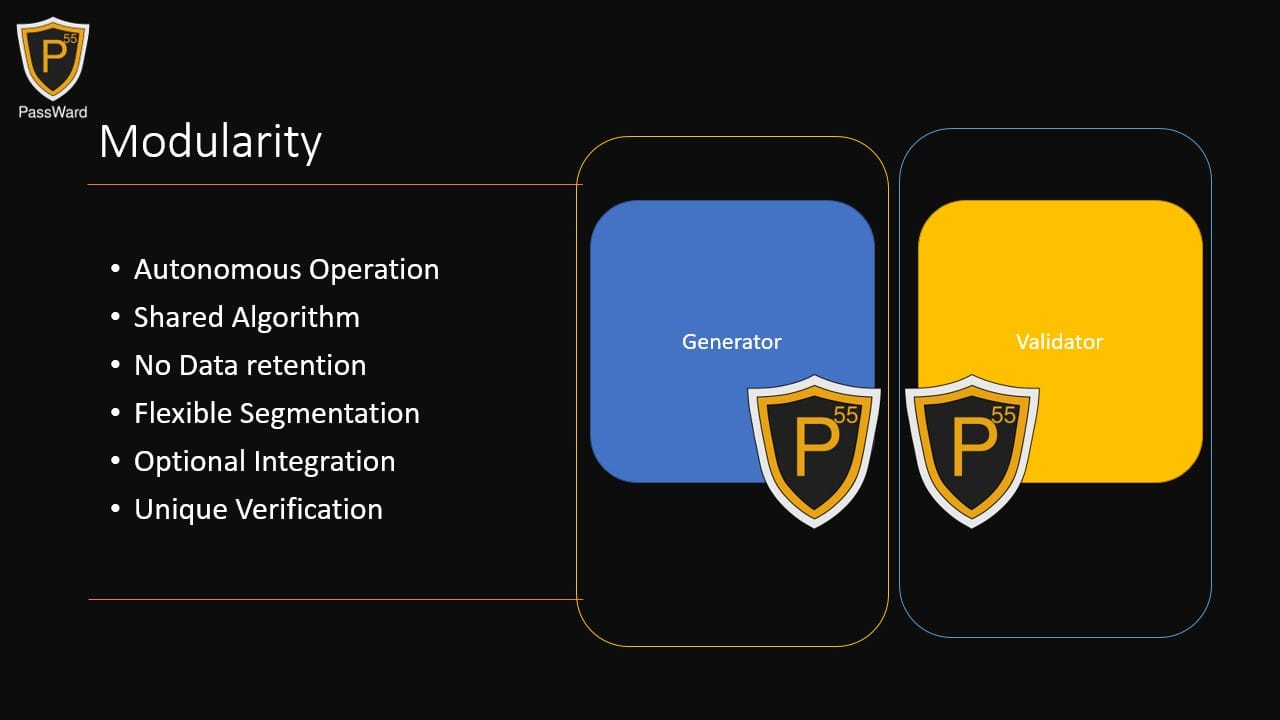
By default, each P55 system uses a unique technology, ensuring no system can be used to compromise another. Yet, it's entirely feasible to employ the same technology across different setups. This modular approach paves the way for innovative and exciting solutions.
This flexibility means a single generator could operate with multiple technology. Similarly, multiple generators could use a single technology. The same principle applies to the validator.
To illustrate this concept, consider the following example. A quick note: while a revocation process and other security measures can be applied to P55 hashes, this example focuses on demonstrating one of the system's many capabilities.
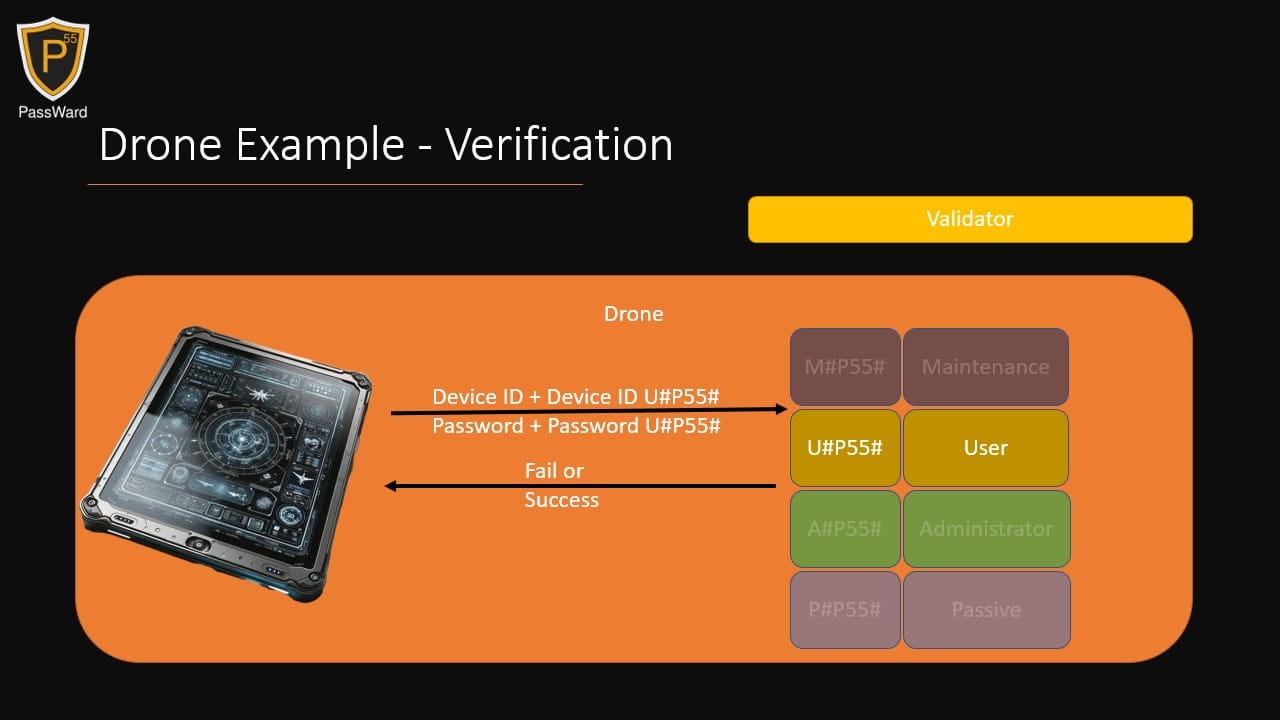
Imagine three isolated locations: a Manufacturer, a Control Center, and a Battlefield.
- The Manufacturer has a generator equipped with the M#P55# technology for Maintenance.
- The Control Center possesses a generator with three technology: U#P55# for User, A#P55# for Administration, and P#P55# for Passive operations.
- On the Battlefield, a drone is equipped solely with a validator carrying all these technology.
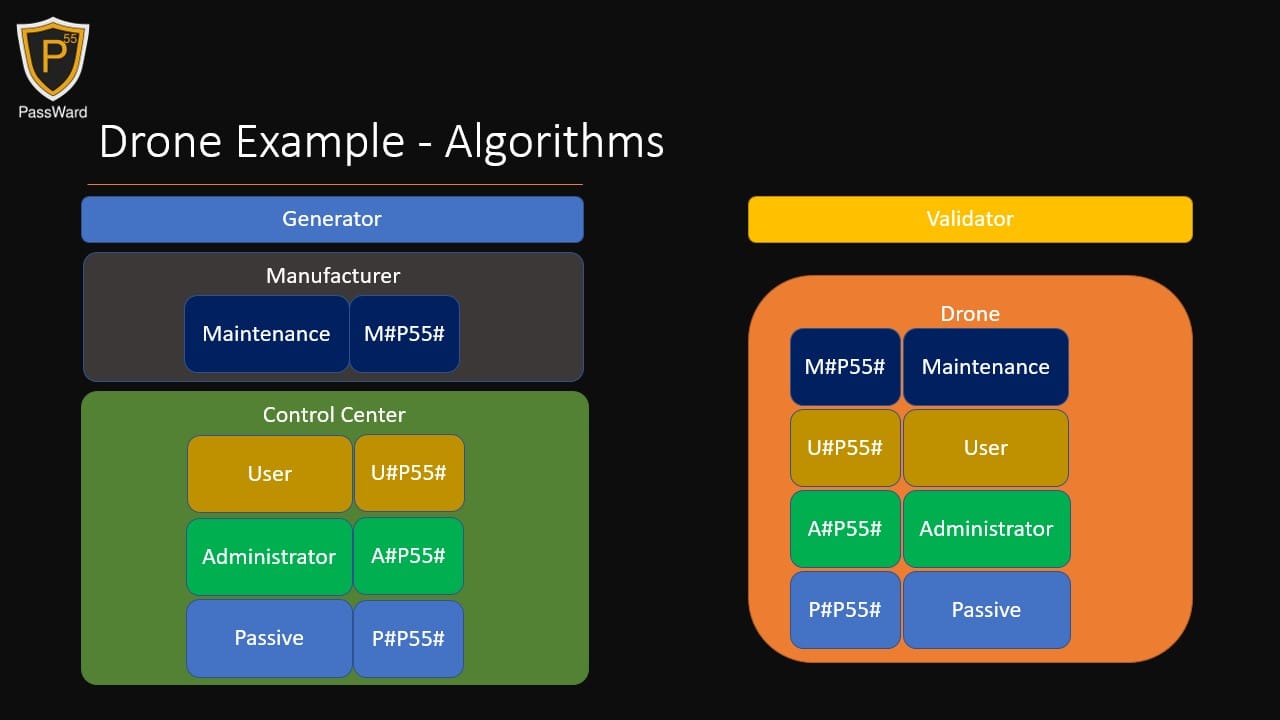
This setup facilitates Role-Based Access Control (RBAC), determined by which P55 technology is used for authentication. If the Manufacturer requires Maintenance, they generate their P55 hashes on-site. Once the drone is deployed, the Control Center uses their Administration technology to restrict this capability. Additionally, when operated by a User, the Control Center can access GPS data using the Passive technology. It's important to note the uniqueness of each technology, ensuring, for instance, that a Passive technology can never function as a User technology, and so forth. Remarkably, no P55 hash is stored in any of these systems. They are only saved on the device interacting with the drone and can be discarded if not reused.
For Multi-factor Authentication, a P55 can also be created based on a calculated or hardware-based Device ID.
If the capabilities and potential of the P55 system have piqued your interest, and you're curious about how it can revolutionize and enhance your security posture, we'd love to hear from you. For a deeper dive into how the P55 system can be tailored to meet your unique security needs, feel free to reach out. We're here to discuss, advise, and help you navigate the complexities of modern cybersecurity. Contact us and let's explore together how the P55 system can be a game-changer for your security strategy.





